Explore / RFID Basics & Resources
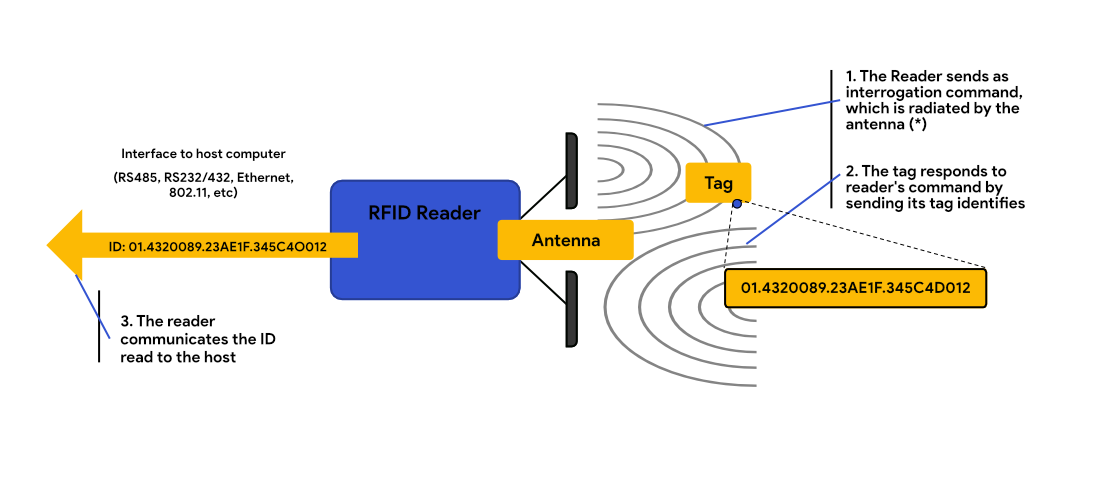
RFID Basics - RFID Reader Interrogation Zone
An interrogation zone (or read zone) consists of the RFID reader (or interrogator), antennas, cables, peripherals, and the environment in which the equipment is installed. The complexity of an interrogation zone is determined by its environment, in which the presence of multiple objects can cause reflections, absorption, or interference with the original signal. These factors can cause unintentional reads, can block the intended reads, and can reduce throughput processing capability.
Hardware and software for an interrogation zone must be properly selected and configured to eliminate or overcome the environmental and business procedural obstacles and limitations. Before you can create a properly functioning interrogation zone, you must understand its components.
INTERROGATOR FUNCTIONALITY
Interrogators (also called readers or transceivers) read and write data to and from tags. Interrogators are responsible for remotely powering the tags (in passive and semi-passive systems), establishing the bidirectional data flow between themselves and the tags, and performing analog to digital as well as digital to analog signal conversion.
Interrogators can also run attached to peripheral devices, such as light stacks or alerting horns that provide feedback on conditions within the system; and triggering devices, which control when the interrogators are turned on and off. Peripherals are usually attached to the I/O ports of the interrogators.
Interrogators can also communicate with and control nearby sensors integrated within the interrogation zone and are responsible for communications over networks for alerting back-end systems of the assets or goods they are tracking.
According to their capabilities, interrogators are often called either smart or dumb. Smart interrogators carry built-in computers that run programs, which filter, aggregate, and analyze data to turn it into meaningful events for the back-end system. A dumb interrogator reads tag data and reports what it sees to the back-end system. This type of interrogator is highly dependent on a middleware product that performs filtering and aggregation functions and converts the data read into a meaningful format, which acts as the input to the back-end system. Most of the interrogators today are smart interrogators.
Interrogators often have a graphical user interface (GUI) by which they can be controlled. An interrogator GUI is typically accessible through a web interface using any commercial Internet browser on the computer or through a simple application program. Following are some typical features of a GUI:
• Read from and write to tag capability
• Network configuration settings
• Antenna settings
• Power settings
• Input/Output port configuration settings
• Firmware upgrade capability
Firmware upgrades on the interrogator are performed to enhance performance, support new features, or resolve issues with the existing platform. They are usually downloaded from the manufacturer’s site and can be deployed to the interrogators in a variety of methods. Most common methods are a Pull method, where the new firmware is downloaded or “pulled” by the reader using File Transfer Protocol (FTP), or Hyper Text Transfer Protocol (HTTP), and an automated Push method, where the new firmware is automatically uploaded or “pushed” to a reader from the host. The method used depends on the manufacturer and middleware used in the installation.
INTERROGATOR COMPONENTS
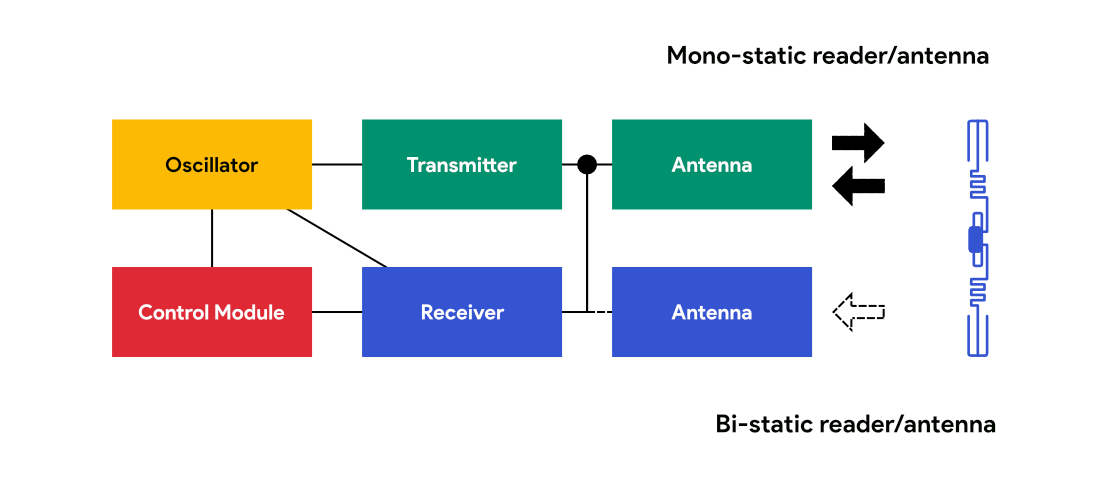
An interrogator includes a transmitter, a receiver, an oscillator and a control unit (processor).
OSCILLATOR
Oscillator provides carrier signal to modulator (in transmitter) and a reference signal to demodulator (in receiver) circuits.
TRANSMITTER
The transmitter part of an interrogator consists of the following:
• Base band transmitter Sends the carrier wave that powers the tags
• Power amplifier Amplifies the signals produced by the oscillator
• Modulator The original RF wave’s amplitude, frequency of transmission, or phase
RECEIVER
The receiver part of an interrogator consists of the following:
• Amplifier Amplifies the weak signals received from the tag before demodulation
• Demodulator Compares the modulated signal to the original signal, thereby extracting the information embedded within
CONTROL UNIT (PROCESSOR)
A processor embedded within the interrogator provides these functions:
• Controls network communications with the middleware or back-end system
• Runs the primary operation systems for the interrogator
• Controls the functions of the interrogator
• Controls the memory (ROM, RAM, hard drive type data storage)
Today, many of these components are contained within a digital signal processor (DSP) so that the radio portion of the interrogator is essentially software-controlled and features can be changed or upgraded on the fly.
The external interfaces to the interrogator are various communication ports such RS-232, RS-245, or RS-422 serial ports; universal serial bus (USB); Bluetooth and 802.11 wireless network interfaces; LAN ports; general purpose I/O ports; and most importantly antenna ports typically found in batches of four or eight antennas, depending on whether the interrogator is monostatic or bistatic.
Interrogators can be powered in different ways. For installations of almost any commercially available interrogator, you will need readily accessible 110 V or 240 V AC outlets (for US and European installations, respectively). Handheld interrogators can utilize an internal battery, but they will have to be recharged using a docking station connected to an AC outlet. In certain situations, it may be appropriate to use Power Over Ethernet (POE), which allows the same wire that transfers data to the interrogator to provide power to it also.
MONOSTATIC VERSUS BISTATIC INTERROGATOR
A monostatic interrogator uses a single antenna to transmit and/or receive data to or from a tag. A circulator that lives inside the interrogator turns the antenna from the transmitting to receiving function in a very rapid manner. A bistatic interrogator uses two antennas, each dedicated either to transmitting or receiving. Bistatic interrogators usually have twice as many antenna ports as monostatic interrogators.
INTERROGATOR TYPES
Interrogators come in multiple formats, and you choose the most appropriate type to match the business process in which you are trying to use this technology. The main types are Fixed interrogators and Mobile Interrogators, which include handheld and vehicle-mounted interrogators. Interrogators can also come in the form of a USB stick for laptops, or module-based interrogators found in RFID-enabled printers.
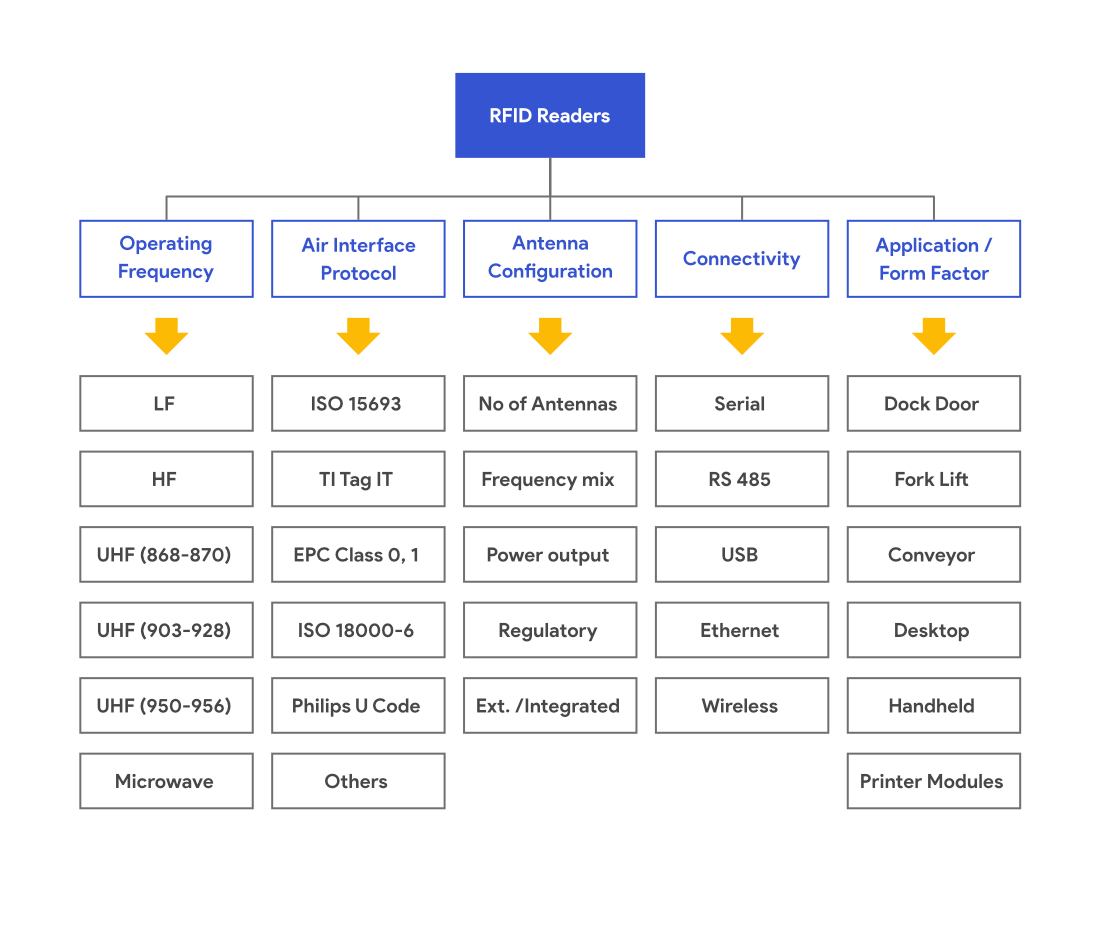
FIXED INTERROGATORS
A monostatic interrogator uses a single antenna to transmit and/or receive data to or from a tag. A circulator that lives inside the interrogator turns the antenna from the transmitting to receiving function in a very rapid manner. A bistatic interrogator uses two antennas, each dedicated either to transmitting or receiving. Bistatic interrogators usually have twice as many antenna ports as monostatic interrogators.
VEHICLE-MOUNTED INTERROGATORS
Vehicle-mounted interrogators, which can automate shipping and receiving of goods, are usually integrated into material handling devices such as forklifts, paper trucks, cargo trucks, and pallet jacks. These interrogators usually have a special shape for easier installation onto the vehicle and a rugged design to survive the vibrations and other environmental conditions.
HANDHELD INTERROGATORS
Mobile interrogators, such as handheld interrogators, are often used for low-volume reading or writing in exception processing, quality assurance, and mobile shipping receiving units. Handheld interrogators come in a variety of forms and have a vast selection of options for communications. They can be tethered, receiving power and accomplishing data transmission via a nearby base unit using an extensible cord. Other types of handhelds can be wireless, depending on wireless networks or Bluetooth communications for data transfer, limiting operational time to battery life between charges. Newer renditions of handheld interrogators are appearing in forms of cellular phones and personal digital assistants (PDAs).
Handheld interrogators are usually monostatic, with integrated linear antennas. The monostatic design keeps their size to a minimum since only one antenna is used, while the linear antenna polarization is used to get the best read range. The interrogator’s orientation can be changed simply by turning your wrist.
INTERROGATOR ANTENNAS
The interrogator antenna is a converter between the radiated waves and wired voltage that feeds the system. It is the largest and most obvious and most exposed point of the system, as it must be near the assets it is identifying. This also makes it the most vulnerable point of the system, because it be physically impacted by goods traversing the interrogation zone. Antennas tend to be near doorways in distribution centers and manufacturing centers so they are occasionally exposed to rain, snow, wind, and high-speed vehicles (such as fork trucks) traveling through the interrogation zone.



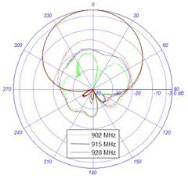
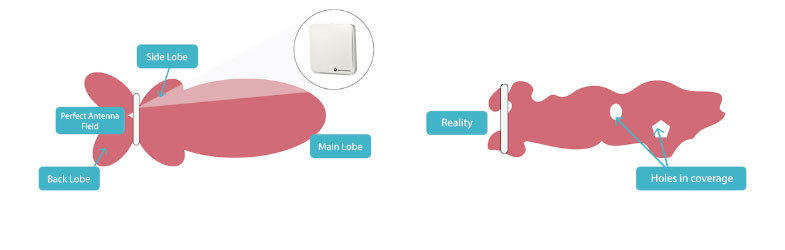
ANTENNA FOOTPRINT
The footprint of the antenna will dictate the size of the interrogation zone and how well the zone will be covered by the antenna. Most antennas come with a radiation plot that defines the area the antenna will cover, how far away the signal can be measured, and how wide the antenna beam is at its widest. Overlapping antenna coverage is always a good idea in fixed interrogator installations to ensure consistent and maximum coverage within the interrogation zone.
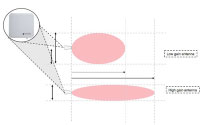
ANTENNA GAIN
The length and width of the read zone will be determined by the gain of the antenna. Antennas with higher gain will have longer and narrower RF pattern. On the other hand, antennas with lower gain will have shorter and wider RF pattern. Most antennas come with standard 8.5 dBi gain, however, you can also get lower and higher gain antennas for special application.
ANTENNA POLARIZATION
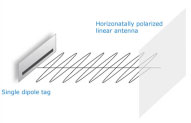
Both linearly and circularly polarized antennas are used in common RFID supply chain applications. Linear antennas propagate only on a single plane, so they are either horizontally or vertically polarized. Linear antennas have a more focused beam than a circular antenna, and as a result, more power is realized on a single plane in the interrogation zone compared to circular antennas. Therefore, linear antennas achieve longer read ranges and better penetration of dense objects than circular antennas.
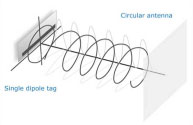
Circularly polarized antennas spread their power equally across a vertical and a horizontal plane; therefore, the signal is not propagated as far and a tag does not receive as much power as it would from a linear antenna, because the power is split across two planes. The main advantage of a circular antenna is, however, that the objects do not need to be in a specific orientation in order to be read.
In a mixed environment where orientation cannot be controlled, circular antennas work best. In a manufacturing environment where orientation can be assured, linear antennas are better because they can penetrate dense objects.
Note: Antennas are neither monostatic nor bistatic, as this is determined by the interrogator. However, they are sometimes referred to in these ways because an antenna that is intended for use in a bistatic interrogator usually consists of two antennas in its casing and is larger in size. Theoretically, this antenna could be used as two monostatic antennas if it were connected to two antenna ports on a monostatic interrogator.
PROTOCOLS
An air interface protocol is the means by which the tag communicates with the interrogator and the interrogator communicates with the tag. Data protocols determine how the interrogator interprets the numbers it reads during this exchange. Air interface protocols and data protocols are governed by various standard bodies such as the International Organization for Standardization (ISO) and EPCglobal, the two primary bodies that define how these protocols work.
For more information about Standards and Protocols visit
INTERROGATION ZONE CONFIGURATION
To make an interrogator function properly, you must configure it properly using settings that differ by the type of the interrogator as well as the manufacturer. Following are the most common settings you may encounter.
• Output power One of the most important settings is the transmit power level of an interrogator. The power level is usually set so that interrogators do not interfere with interrogation zones installed parallel to one another. Power levels will be usually provided in watts (W), milliwatts (mW), decibels (dB) or as a percentage, where 100 percent will equal to 1 W (or the maximum allowed power for that region of the world). In certain situations, you may be able to adjust both the reading power and writing power.
• Antenna settings You can combine antennas into groups within the configuration of an interrogator. This allows multiple antennas to act as a single device, pushing more power into the interrogation zone to flood the area with a signal and ensure that all tags in that area are read. In many cases, you can also choose antenna sequencing, which allows multiple antennas to operate in a particular order.
• Retries You can set up the number of times an interrogator will attempt to find new tags in the interrogation zone before reporting its findings. This is known as retries.
• Filtering This feature allows the interrogator to communicate only with the portion of the tag population it is looking for. For instance, a dock door interrogator may filter out all case tags and communicate results from pallet tags only.
• Polling Interrogators can scan for tags either continuously, in preset intervals, or on demand.
• Modes of reading Sometimes you can choose from various modes of reading that are already preset to ensure a specific interrogator performance. You can encounter a conveyor mode, self-mode, or rapid read mode, and although manufacturers use different terms to refer to these modes, they all are basically the same for all interrogators.
For instance: When in conveyor mode, the interrogator reads in fast intervals with a low number of retries; in this mode, usually few tags are in the interrogation zone but they need to be read quickly, since the tag is in view of the antenna for only a short time. Inventory mode is more of a transitional mode. The interrogator will report when it sees a change; it will see a large number or a given number of tags for a specific amount of time, and when that number changes, the interrogator instantly generates a report to the back-end system to indicate the loss or gain of a new tag identity.