Explore / RFID Basics & Resources
RFID Basics - EPC Gen2 Memory
As per How to Select a Correct RFID Tag – Standards & Mandates, this standard is officially called EPC Radio-Frequency Identity Protocols Class 1 Generation 2 UHF RFID protocol for communications at 860–960 MHz. It was developed by EPCglobal, Inc. in 2004, which is now GS1, and was approved as ISO 18000-6C in July 2006. It defines air interface parameters for tags operating within the frequency range of 860–960 MHz and allows for use of different frequencies in different regions from within this range.
There are several versions of this standard and the latest version Gen2v2 (that was first introduced in 2013) 2.0.1. (ratified in 2015) introduces several new features to the protocol.
THE TABLE BELOW PROVIDES AN OVERVIEW OF GENERATION2 FEATURES:
EPC Gen2 Requirement
Global regulatory compliance
Memory access control
Read speed
Dense-reader operation
Anti-collision
Kill security
Memory-write capability
Bit-masked filtering
User Memory
Cost and availability
Authentication
Traceability
EPC Gen2 (v2) Features
Europe, North America, and others
32-bit Access password Memory locking
Greater than 1,000 tags per second
Dense-reader operating mode
Flexible, changing based on environment
32-bit Kill password
Greater than seven tags per second write rate
Flexible Select command
Size based on vendor, enhanced for logging
Multi-vendor available, low cost
Cryptographic authentication for anti-counterfeiting
Functions for Untraceability
For more information, read How to Select a Correct RFID Tag – Standards & Mandates.
TYPES OF DATA IN GEN2 TAG MEMORY
| Information Type | Description | Where on Gen 2 Tag | Where Typically Used | Bar Code Equivalent |
|---|---|---|---|---|
| Business Data | Describes the physical object to which the tag is affixed. | EPC Bank (excluding PC and XPC bits, and filter value within EPC) User Memory Bank | Data Capture layer and Business Application layer | Yes: GS1 keys, Application Identifiers (AIs) |
| Control Information | Facilitates efficient tag interaction MIC | Reserved Bank EPC Bank: PC and XPC bits, and filter value within EPC | Data Capture layer | No |
| Tag Manufacture Information | Describes the tag itself, as opposed to the physical object to which the tag is affixed. | TID Bank | Data Capture layer Unique tag manufacture serial number may reach Business Application layer | No |
GENERATION 2 MEMORY LAYOUT
The following graphic depicts the Generation 2 memory layout. Gen2 tags can four banks of non-volatile memory – Reserved Memory, EPC Memory, Tag Identification (TID) Memory and User Memory. Each memory region is accessed in parts, that are 16-bit long, called words, starting at word 0.
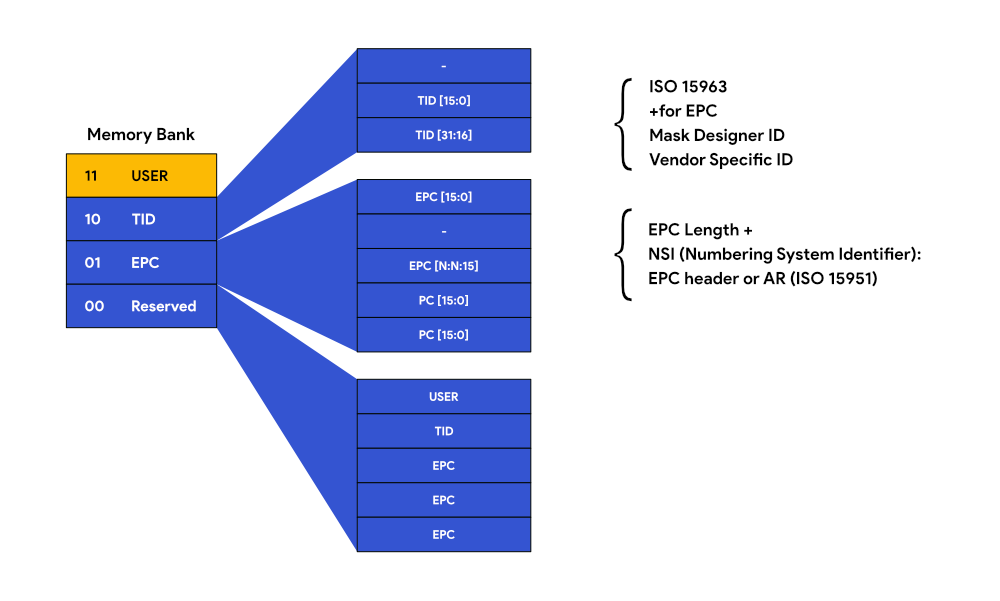
RESERVED MEMORY (BANK 0)
The reserved area of memory holds the tag’s Access and Kill passwords, with a 32-bit “Kill” password that allows a tag to be permanently silenced.
• The Kill command only executes if the password has been set (that is, is non-zero).
• The default Kill password value is zero.
A 32-bit Access password allows the Tag to transition to the Secured state. A tag in the Secured state can execute all Access commands, including writing to locked blocks.
Kill and access passwords must be accepted prior to being used. The kill password is a 32-bit value stored in reserved memory 00h to 1Fh, MSB first. Remember that:
• A tag that does not implement a kill password acts as though it had a zero-valued kill password that is permanently read/write locked.
• A tag does not execute a kill operation if its kill password is zero.
• An interrogator uses a tag’s kill password once, to kill the tag and render it silent thereafter.
• The default (that is, un-programmed) value is zero.
The access password is a 32-bit value stored in reserved memory 20h to 3Fh, MSB first. Remember that:
• Tags with a non-zero access password is required an interrogator to issue this password before transitioning to the secured state.
• The default (that is, un-programmed) value is be zero.
A tag that does not implement an access password acts as though it had a zero-valued access password that is permanently read/write locked.
EPC MEMORY (BANK 1)
EPC Memory consists of the 16-bit Cyclic Redundancy Check (CRC-16), which is an error detection code, a 16-bit Protocol Control (PC) and starting with Word 2, the EPC number (96 to 496 bits).
The Protocol Control manages, how many bits of EPC are sent back to the reader, regardless the actual length of the EPC data in the bank. The standard is 96 bits but what if you need to send more? The length is defined in the PC. The total amount of words for EPC data in the memory depends on the chip manufacturer.
The PC is further subdivided:
• First 5 bits indicate the EPC memory length, next bit indicates whether the tag has or does not have user memory.
• The bit 6 identifies the existence of the Extended Protocol Control Word 1 (XPC_W1) in the word 21 of EPC Memory.
• The bit 7 identifies whether the data in the EPC data area conforms to a GS1 EPCGlobal™ (set to 0b) or an ISO/IEC 15961 coding scheme (set to 1b). The actual coding scheme is identified in the Application Family Identifier (AFI) bit field.
| Bits | Field | Description | Where Specified |
|---|---|---|---|
| 10h–14h | Length | Represents the number of 16-bit words comprising the PC field and the EPC field (below). See discussion in Section 15.1.1 for the encoding of this field. | UHFC1G2 Standard |
| 15h | User Memory Indicator (UMI) | Indicates whether the user memory bank is present and contains data. | UHFC1G2 Standard |
| 16h | XPC Indicator (XI) | Indicates whether an XPC is present | UHFC1G2 Standard |
| 17h | Toggle | If zero, indicates an EPCglobal application; in particular, indicates that bits 18h – 1Fh contain the Attribute Bits and the remainder of the EPC bank contains a binary encoded EPC. If one, indicates a non-EPCglobal application; in particular, indicates that bits 18h – 1Fh contain the ISO Application Family Identifier (AFI) as defined in [ISO15961] and the remainder of the EPC bank contains a Unique Item Identifier (UII) appropriate for that AFI. |
UHFC1G2 Standard |
| 18h–1Fh(if toggle = 0) | Attribute Bits | Bits that may guide the handling of the physical object to which the tag is affixed. (Applies to Gen2 v 1.x tags only.) | Section 11 of EPC C1G2 Tag Data Standard |
| 18h–1Fh(if toggle = 1) | AFI | An Application Family Identifier that specifies a non-EPCglobal application for which the remainder of the EPC bank is encoded | ISO 15961 |
USER MEMORY (BANK 3)
User memory is optional and can have various sizes, usually 512 bits and up to 4 or 8K of memory in some tags. This memory is used for additional data that is not suitable or does not fit into the EPC memory, such as for instance temperature or maintenance logs, expiration dates and other data.
The first few bits are a Data Storage Format Identifier (DSFID) as specified in ISO15961 and ISO15962. The DSFID specifies the format for the remainder of the user memory bank. The DSFID is usually eight bits in length, but may be extended as per ISO15961. When the DSFID specifies Access Method 2, the format of the remainder of user memory is “packed objects”. This format is recommended for use in EPC applications.
TAG IDENTIFICATION (TID) MEMORY (BANK 2)
TID Memory carries the unique tag identifier that cannot be changed or erased. This ID identifies the tag itself, rather than item it is applied to.
EPC TAG DATA STANDARDS, VERSION 1.9 (PUBLISHED JULY 2014)
This standard defines EPC tag data formats for Generation 2 tags. It defines how the EPC is encoded on the tag and how it is encoded for use in the information systems layers of the EPC Systems Network. The standard includes specific encoding schemes for EPC General Identifier (GID).
extended as per ISO15961. When the DSFID specifies Access Method 2, the format of the remainder of user memory is “packed objects”. This format is recommended for use in EPC applications.
GID FORMAT
Decimal capacity0011 0101(actual value)268,435,45516,777,21536 bits
| Information Type | HEADER | GENERAL MANAGER NUMBER | OBJECT CLASS NUMBER | SERIAL NUMBER |
|---|---|---|---|---|
| GID-96 | 8 bits | 28 bit | 24bit | 24 bits |
The standard also defines encoding of other numbering systems for 96 bits used in global trade.
OTHER EPC SCHEMES
This standard defines EPC tag data formats for Generation 2 tags. It defines how the EPC is encoded on the tag and how it is encoded for use in the information systems layers of the EPC Systems Network. The standard includes specific encoding schemes for EPC General Identifier (GID).
extended as per ISO15961. When the DSFID specifies Access Method 2, the format of the remainder of user memory is “packed objects”. This format is recommended for use in EPC applications.
GID FORMAT
| Information Type | HEADER | GENERAL MANAGER NUMBER |
|---|---|---|
| SGTIN | Serialized Global Trade Item Number | Used to assign a unique identity to an instance of a trade item, such as a specific instance of a product or SKU. |
| SSCC | Serial Shipping Container Code | Used to assign a unique identity to a logistics handling unit, such as the aggregate contents of a shipping container or a pallet load. |
| SGLN* | Global Location Number (with or without extension) | Used to assign a unique identity to a physical location, such as a specific building or a specific unit of shelving within a warehouse. |
| GRAI | Global Returnable Asset Identifier (serial number mandatory) | Used to assign a unique identity to a specific returnable asset, such as a reusable shipping container or a pallet skid. |
| GIAI | Global Individual Asset Identifier | Used to assign a unique identity to a specific asset, such as a forklift or a computer. |
| GSRN | Global Service Relation Number (for Recipient) | Used to assign a unique identity to a service recipient, i.e. a Hospital Patient or a Club Member. |
| GSRNP | Global Service Relation Number for Provider | Used to assign a unique identity to a service provider, i.e. a hospital or a club. |
| GDTI | Global Document Type Identifier | Used to assign a unique identity to a specific document, such as land registration papers, an insurance policy, etc. |
| CPI | Component / Part Identifier | Used by the technical industries (including the automotive sector) for the unique identification of parts or components. |
| SGCN | Serialized Global Coupon Number | Used to uniquely identify a coupon. |
| GID | General Identifier | The GID EPC scheme is independent of any specifications or identity scheme outside the EPCglobal Tag Data Standard. |
| DOD | US Department of Defense Identifier | Defined by the United States Department of Defense. This tag data construct may be used to encode 96-bit Class 1 tags for shipping goods to the United States Department of Defense by a supplier who has already been assigned a CAGE (Commercial and Government Entity) code |
| ADI | Aerospace and Defense Identifier | Used by the aerospace and defense sector for the unique identification of parts or items. |
*Explanation: Note that the letter “S” in the term “SGLN” does not stand for “serialized” as it does in SGTIN. This is because a GLN without an extension also identifies a unique location, as opposed to a class of locations, and so both GLN and GLN with extension may be considered as “serialized” identifiers. The term SGLN merely distinguishes the EPC form, which can be used either for a GLN by itself or GLN with extension, from the term GLN which always refers to the unextended GLN identifier. The letter “S” does not stand for anything. (Source GS1.org)