Explore / RFID Basics & Resources
RFID Anti-Collision and Dense Reader Mode
Let’s discuss various standards related to the design and use of RFID systems as well as a few RFID mandates issued by some commercial and governmental organizations, which drive a large part of RFID implementations today.
Standards are created by various organizations to facilitate interoperability among components of the system designed and manufactured by many different organizations. Many organizations develop standards—for example, the International Organization for Standardization (ISO), American National Standards Institute (ANSI), and EPCglobal.
While more than one standard may be available for a particular use and compliance with it is optional, regulations must be obeyed. Mandate compliance is optional. Mandates are created by organizations as a policy to interact with various business partners. The following sections describe various RFID standards and mandates that will effect the selection of a particular tag.
READER TO READER INTERFERENCE
While tag to tag interference is called collision and it is usually prevented by an RFID anti-collision algorithm, the reader to reader interference is usually prevented by the RFID dense reader mode.
The near-field readers use magnetic flux to communicate with the tags. The magnetic flux decays very rapidly and since the near-field readers are usually not installed very close to each other they do not interfere with each other.
Reader-to-reader interference is only an issue for ultra-high frequency (UHF) and microwave readers operating in far-field. Reader interference countermeasures include:
• Physical isolation
• Absorptive materials
• Shielding
• Reduced transmit power
• Frequency hopping
• Band separation
The ISO/IEC 18000 series of standards has seven parts and deals only with the air interface protocol. The standards define use of five frequency bands for communication between interrogator and tags. Let’s review only the most important parts.
When a reader and tag transmission share a channel, reader transmission is 100 dB larger than tag backscatter. The distant in-channel readers mask nearby tags. To solve this problem Generation 2 protocol provides three reader operation levels as follows:
ENVIRONMENT
Single-Reader
Multiple-Reader
Dense-Reader
DESCRIPTION
A single reader operating in the environment
# of simultaneously active readers < # of available channels
Example: 10 readers operating in 50 channels
# of simultaneously active readers » # of available channels
Example: 50 readers operating in 50 channels
The number of available channels in US is 50, while in Europe it is 20.
Interference is mitigated by the environment and the modes in which the interrogators operate. Single interrogator environments obviously indicate one interrogator is installed in a particular facility. This interrogator can broadcast on whatever channels it finds appropriate within its configuration at any given time. The interrogator will not encounter interference from other interrogators, but it may encounter interference from the environment and from its own multi-path interference caused by reflections of its own or other signal(s). This type of interference can be handled by proper shielding and by adjusting the signal strength and antenna gain (the gain is not adjustable on the antenna itself, you’d have to switch to a different antenna).
If the number of simultaneously operating interrogators is smaller than the number of available channels, a multiple interrogator environment results. In this type of environment, the interrogators can interfere with each other, but you can resolve this by assigning specific channels to specific interrogators or by time division.
In a dense interrogator environment, the number of interrogators operating is greater than the number of available channels. Certified interrogators will incorporate schemes identified in the Gen 2 specification to minimize mutual interference.
Note: In order to handle a dense interrogator environment successfully, it is essential that all interrogators operate in dense interrogator mode. If one interrogator does not operate in this mode, the whole scheme will not work.
DENSE INTERROGATOR MODE
Dense interrogator mode (often called dense reader mode) allows for operation of multiple interrogators located within close proximity of each other without causing interrogator interference. Dense interrogator mode can also involve special allocations in which interrogators and tags are separated in their ability to communicate on various channels so that strong interrogator signals will not overpower weaker tag responses.
Interrogators that are EPC Gen 2 certified use dense interrogator mode when the number of interrogators present in an environment exceeds the number of available channels. In North America, dense interrogator mode is used if more than 50 interrogators are installed within a facility. In Europe, the mode is used if the number of operating interrogators is greater than 10 if they operate at maximum allowed power.
Dense interrogator mode allows for coordination of interrogators so that no two interrogators are transmitting at the exact same moment on exactly same frequency and causing interference within one another’s interrogation zones. To do this, many interrogators perform frequency hopping and support a function known as listen before talk (LBT).
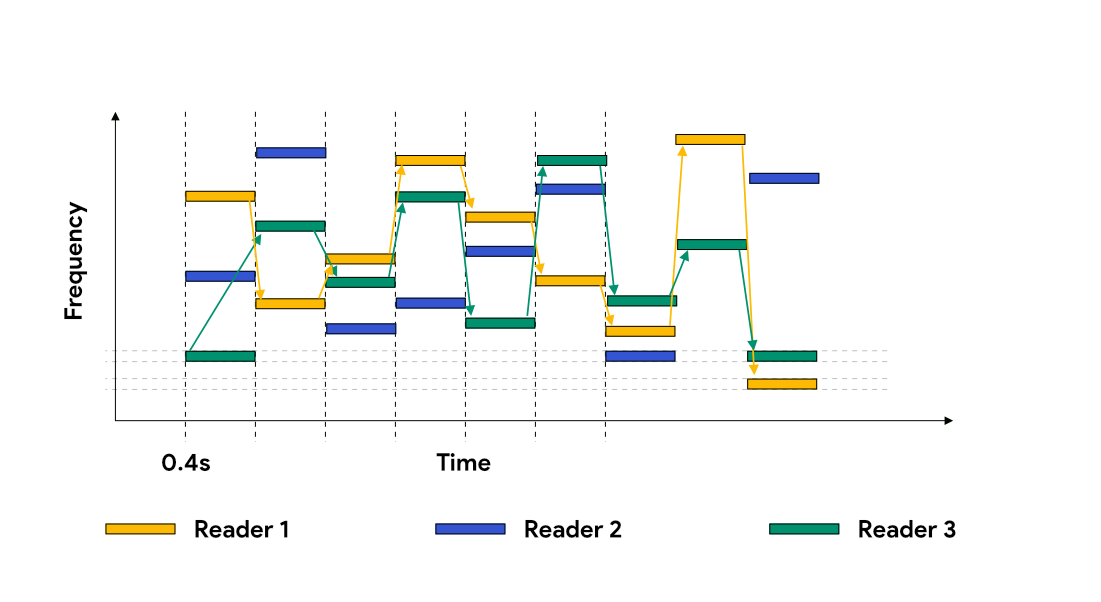
Frequency Hopping and LBT
Frequency hopping employs a technology that forces an interrogator to change channels constantly within a given range of frequencies. For instance, a UHF interrogator licensed by the FCC for operation in North America must support hopping across 50 channels (each 500 kHz wide) between the frequencies of 902 to 928 MHz and spend no longer than 0.04 second in any channel during this rotation.
To perform LBT, interrogators use an antenna (often a dedicated antenna) to listen for the frequency on which the interrogator is about to transmit. If another interrogator is communicating in that channel, the interrogator will automatically switch to the next available channel and transmit there instead. LBT is often used with frequency hopping and is required in Europe for dense interrogator operations.
Other forms of dense interrogator mode include spectral allocation, time slice interrogator control, software synchronization, and hardware timing controls of interrogator platforms.
Spectral allocation designates a portion of the allotted frequency range for each type of communication. This allows tags to talk in different channels than interrogators, which prevents them from interfering with one another.
Time slice interrogator control is typically done with a back-end system controller that determines when each interrogator is allowed to communicate. In this method, each interrogator is provided a set period of time for communication, and it is then turned off to wait for its next turn while all the other interrogators communicate.
Software synchronization allows the interrogators to communicate with one another and determine which one can transmit at what time via software built into the interrogator’s operating system.
Hardware timing will usually employ the use of triggering devices to allow interrogators to communicate for controlled periods of time. For instance, when an object breaks a light beam on the way into the interrogation zone, the read cycle is started. As the object leaves the interrogation zone, it breaks another beam that tells the interrogator to stop.
TAG POPULATION MANAGEMENT
Interrogators support various commands and functions used for managing the tag population. They can address an entire group of tags to perform inventory of all tags in the area, as well as singulate each tag to access its memory and perform reading and writing operations.
The following are the most important interrogator commands:
• Select Used to determine which groups of tags will respond (for example, this command can be used to isolate case tags from item tags).
• Inventory Used to identify individual tags within a group.
• Access Used to communicate with individual tags and issue commands to them once they have been singulated.
• Kill After the tag has been accessed and a secure communication channel established, this command can be used to make the tag stop functioning. Killed tags will not respond to interrogation and cannot be resurrected.
• Lock Used to secure the contents of a tag. Once issued, it can prevent the tag from being read from or written to. Can also be used to lock individual tag memory banks.
• For more information on Interrogator Commands, visit Gen2 Reader Commands and Q Parameter.
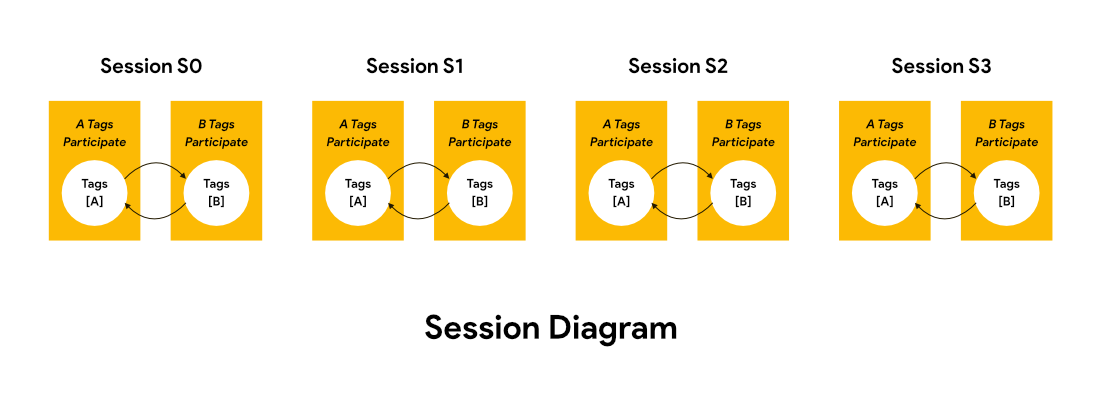
Sessions and AB Symmetry
Generation 2 interrogators support these interrogator commands and also tag management functions, such as AB symmetry and sessions.
AB symmetry replaced the Gen 1 technique of “putting tags to sleep” after being interrogated. AB symmetry allows tags to be flagged with an identifier to ease counting. If a tag that was flagged as an A gets counted, it then becomes flagged with a B until it is counted again, at which time it will be flagged with an A. This technique eliminates problems with tags that cannot “wake up” or are slow to wake up for the next round of inventory.
Gen 2 tags support four sessions. This function is used when more interrogators or groups of interrogators interrogate the same group of tags. A tag would use each session to communicate with one interrogator or group of interrogators. This way, if a tag communicates with one interrogator and has been flagged with a B, for instance, a second interrogator communicating with the tag will use a second session with its own A and B flags. This will prevent the interrogators from interfering with each other’s inventory rounds and avoid confusion that may cause an interrogator to count a tag twice.
ANTI-COLLISION
The various types of RFID anti-collision methods can be reduced to two basic types: deterministic and probabilistic. An example of deterministic is binary tree algorithm or tree walking algorithm. An example of probabilistic is the ALOHA anti-collision algorithm.
PROBABILISTIC ALGORITHM
In a probabilistic method, tags respond at randomly generated times. If a collision occurs, colliding tags will have to identify themselves again after waiting a random period of time based on a random number the tag selects. This process will eventually isolate and identify all the tags in the interrogation zone but could be prone to collisions since it is possible that tags could choose numbers too close to one another. However, this algorithm is usually adjustable based on number of tags in the interrogation zone to increase efficiency and decrease collisions. Gen2 interrogators use Slotted ALOHA algorithm. For more information about Slotted ALOHA visit Gen2 Reader Commands and Q Parameter.
DETERMINISTIC ALGORITHM
The deterministic algorithm works by asking for bits on the tag ID, and only tags with matching IDs respond. It starts by asking for the first numbers of the tag until it gets matches for tags; then it continues to ask for additional characters until all tags within the region are found. This method is slow but ultimately leads to fewer collisions and a more accurate search for tags in the interrogation zone.